
|

|
 |
ScrambleSuit
A Polymorphic Network Protocol to Circumvent CensorshipSummary
Free and open communication on the Internet is endangered and censorship is on the rise. In particular, deep packet inspection (DPI) technology is increasingly used to filter what censors consider undesired information. DPI enables fine-grained and cost-effective censorship of entire countries. Accordingly, several countries are documented to use DPI to conduct surveillance, or to block the Tor anonymity network.
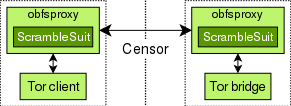
This project at Karlstad University investigated countermeasures to DPI-based censorship. We designed and developed ScrambleSuit, a transport protocol that is particularly hard for DPI boxes to recognise and block. The diagram to the right illustrates The Big Picture. ScrambleSuit is designed as a Python module for obfsproxy, which is an obfuscation framework developed by The Tor Project. Both, the censored client and the server it is connecting to run obfsproxy's ScrambleSuit module. All exchanged network traffic is then encrypted, authenticated, and disguised. Technically speaking, our protocol provides two core features:
- ScrambleSuit protects against active probing attacks. This attack—pioneered by the Great Firewall of China—is an effective and cheap way for DPI boxes to identify encrypted protocols while at the same time minimising collateral damage.
- Our protocol further implements morphing techniques that make it possible for every ScrambleSuit server to generate a unique flow signature. In particular, we alter packet inter-arrival times and the transported protocol's packet length distribution.
Note that despite the diagram to the right, ScrambleSuit is independent of its transported application. While we designed ScrambleSuit specifically for the use with Tor, it can transport any application that supports SOCKS. This includes Tor, VPN, SSH, and many other protocols.
This project was supported by a research grant from Internetfonden, which is part of the Swedish Internet Infrastructure Foundation.
Papers
Before the final, peer-reviewed paper listed below, we published a technical report in May 2013. Several important design aspects have changed since then, so we strongly recommend reading the WPES version instead. Furthermore, you can also find the paper “Towards a Censorship Analyser for Tor” listed below, which was also created during the lifetime of this project. If you are interested in implementing the ScrambleSuit protocol, have a look at our protocol specification.
-
ScrambleSuit: A Polymorphic Network Protocol to Circumvent Censorship
[bibtex]
Philipp Winter, Tobias Pulls, and Juergen Fuss
In the Proceedings of WPES, ACM, 2013 -
Towards a Censorship Analyser for Tor
[bibtex]
Philipp Winter
In the Proceedings of FOCI, USENIX Association, 2013
Code
ScrambleSuit is part of Tor Browser. After downloading Tor Browser, you can get ScrambleSuit bridges from BridgeDB. That's all you need. Note that ScrambleSuit has a successor, obfs4, which is also part of Tor Browser. We recommend that you use obfs4 instead.
You might also be interested in ScrambleSuit's code. It is part of The Tor Project's obfsproxy. You can get a copy of obfsproxy by running
git clone https://git.torproject.org/pluggable-transports/obfsproxy.git
Finally, the measurement tools we used to create some of our paper's graphs are also available online.
Contact
For questions or remarks of any kind, please contact Philipp using phw at nymity dot ch. You can use OpenPGP to encrypt emails.

