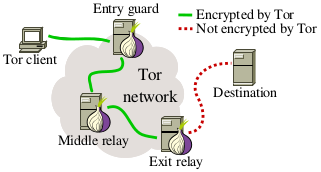
As of April 2014, the Tor anonymity network consists of 4,500 relays of which almost 1,000 are exit relays. As the diagram to the right illustrates, exit relays bridge the gap between the Tor network and the “open” Internet. As a result, exit relays are able to see anonymised network traffic as it is sent by Tor clients.
While most exit relays are honest and run by well-meaning volunteers, there are exceptions: In the past, some exit relays were documented to have sniffed and tampered with relayed traffic. The exposed attacks included mostly HTTPS man-in-the-middle (MitM) and SSL stripping.
In this research project, we were monitoring all exit relays for several months in order to
expose, document, and thwart malicious or misconfigured relays. In particular, we monitor exit
relays with two scanners we developed specifically for that purpose:
exitmap and
HoneyConnector. Since September 2013, we discovered 65
malicious or misconfigured exit relays which are listed in Table 1 and Table 2 in our
research paper. These exit relays engaged in various attacks such as
SSH and HTTPS MitM, HTML injection, SSL stripping, and traffic sniffing. We also found exit
relays which were unintentionally interfering with network traffic because they were subject to
DNS censorship.
Now what do our results mean for regular Tor users? While 65 “spoiled onions” sounds like a large number, it is in fact a rather small number when you consider the size of the set of Tor exit relays: while the Tor network consists of around 1,000 exit relays at any given point in time, the overall number is higher considering the network's churn rate (see Section 5.7 in our research paper). As a result, the probability of encountering a malicious exit relay is small. In addition, TorBrowser contains useful extensions such as HTTPS-Everywhere and NoScript which are able to protect against several attacks. Finally, as the Tor Project says, plaintext over Tor is still plaintext.
This research project was joint work between the PriSec group at Karlstad University in Sweden and SBA Research in Austria. The project was partially funded by a research grant provided by Internetfonden as well as by COMET K1, FFG – Austrian Research Promotion Agency.
The main outcome of our research project was published in PETS'14. Martin presented our paper and the presentation is also available online. In January 2014, we also published a technical report which discusses preliminary findings. However, we strongly recomment reading the PETS version instead as it is more comprehensive and up-to-date.
-
Spoiled Onions: Exposing Malicious Tor Exit Relays
[pdf, bib]
Philipp Winter, Richard Köwer, Martin Mulazzani, Markus Huber, Sebastian Schrittwieser, Stefan Lindskog, and Edgar Weippl
In: Privacy Enhancing Technologies Symposium, Springer, 2014 -
Spoiled Onions: Exposing Malicious Tor Exit Relays (Techreport)
[pdf, bib]
Philipp Winter and Stefan Lindskog
Technical Report, Karlstad University, 2014
Our exit relay scanner exitmap is freely available under the
GPLv3 license. It is written in pure Python and
makes use of the library Stem. The
scanner comes with some modules included but if you decide to write your own module,
please contact us so we can include it in the main repository.
Note that if your module makes use of standalone tools such as
OpenSSH, you will need to use
our patch for
torsocks.
You can get a copy of exitmap from
GitHub:
git clone https://github.com/NullHypothesis/exitmap.git
Our sniffing detector HoneyConnector is hosted at
GitHub and can be downloaded as
shown below. It is also released under the GPLv3
license.
git clone https://github.com/mmulazzani/HoneyConnector.git
Our Torbutton patches are also available on GitHub. Please note that the patches are highly experimental and should only be understood as proof of concept. As a result, the code is incomplete and not safe for practical use.
git clone -b multicircuit_verification https://github.com/NullHypothesis/torbutton.git
Last updated: 2016-04-11




