Tor Browser version 6.0.6 was released two days ago. When collecting traffic traces for website fingerprinting attacks one wants to avoid network traffic not related to a website visit, since noise in the data interferes with the attacks. This post is a walkthrough on how to configure a fresh copy of Tor Browser version 6.0.6 to generate almost no unnecessary network traffic when using a basket2 pluggable transport.
NOTE THAT THE FOLLOWING CHANGES ARE BAD FOR SECURITY AND PRIVACY, AND SHOULD IN NO WAY BE USED FOR REGULAR USE OF TB. E.G, AUTOMATIC UPDATES WILL BE DISABLED.
Prerequisites
We assume you have access to a basket2 server and manually add basket2proxy to Tor Browser. Presumably, the steps below work just well without configuring and using a pluggable transport, but we haven’t tested in detail. We use a basket2 server since it’s the focus of the basketcase. You can find the Tor projects description on bridges here.
Guide
Download Tor Browser, extract it somewhere, and run it. After selecting to connect directly to the Tor network you should see something like this:
Close Tor Browser and open /Browser/TorBrowser/Data/Tor/torrc. For our
basket2 server, running on 192.168.60.184:11111, the entire file looks like
this:
LogTimeGranularity 1
UseBridges 1
UseMicrodescriptors 1
Bridge basket2 192.168.60.163:11111 E6E0EF7165D4D2D1BAB64D901C66F077AAE57443 basket2params=0:0001:VNGwjMiZCARpZCADPh2okaRyzbkcwbxfbjz+oeVkxU8
ClientTransportPlugin basket2 exec ./TorBrowser/Tor/PluggableTransports/basket2proxy -enableLogging=true -logLevel DEBUG -paddingMethods NullOpen Tor Browser to verify that the pluggable transport is working. Close Tor Browser again and launch your favourite packet capture tool. I’ll use Wireshark so we get pretty pictures. With Wireshark and an appropriate IP-based filter running (the IP of the bridge), start Tor Browser again. After about 60 seconds of idle, Wireshark shows:
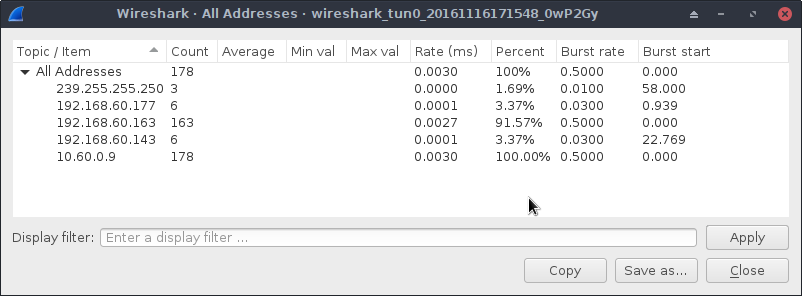
So about 163 packets back and forth. Note that this is with a cached consensus from the previous runs (thanks to the use of micro descriptors above, soon not needed). Let’s see if we can do better.
Start Tor Browser and follow all steps in Mozilla’s guide on How to stop Firefox from making automatic connections. Once done close Tor Browser, restart Wireshark, and launch Tor Browser again. After about 60 seconds we get:
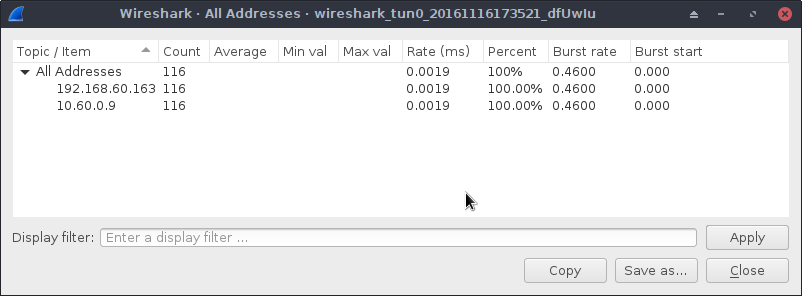
Down to 116 packets, progress! Next, close Tor Browser and open Browser/TorBrowser/Data/Browser/profile.default/preferences/extension-overrides.js. At the bottom, but the following:
# update urls (point all to localhost)
user_pref("extensions.update.background.url", "localhost");
user_pref("extensions.update.url", "localhost");
user_pref("xpinstall.signatures.devInfoURL", "localhost");
user_pref("browser.aboutHomeSnippets.updateUrl", "localhost");
user_pref("noscript.subscription.trustedURL", "localhost");
user_pref("noscript.subscription.untrustedURL", "localhost");
user_pref("extensions.torbutton.test_url", "localhost");
user_pref("extensions.torbutton.test_url_interactive", "localhost");
user_pref("extensions.torbutton.versioncheck_url", "localhost");
# update timers (move far into the future)
user_pref("app.update.lastUpdateTime.xpi-signature-verification", "2476106725");
user_pref("app.update.lastUpdateTime.search-engine-update-timer", "2476106725");
user_pref("app.update.lastUpdateTime.experiments-update-timer", "2476106725");
user_pref("app.update.lastUpdateTime.browser-cleanup-thumbnails", "2476106725");
user_pref("app.update.lastUpdateTime.background-update-timer", "2476106725");
user_pref("app.update.lastUpdateTime.addon-background-update-timer", "2476106725");
user_pref("idle.lastDailyNotification", "2476106725");
user_pref("app.update.timerMinimumDelay", 31536000);
user_pref("datareporting.healthreport.nextDataSubmissionTime", "2476194415800");
user_pref("datareporting.policy.firstRunTime", "2476194415800");
user_pref("noscript.subscription.lastCheck", "2476106725");
user_pref("extensions.torbutton.lastUpdateCheck", "2476106725");
user_pref("app.update.lastUpdateTime.blocklist-background-update-timer", "2476106725");
# disable updates
user_pref("extensions.blocklist.enabled", false);
user_pref("browser.safebrowsing.downloads.remote.enabled", false);
user_pref("app.update.auto", false);
user_pref("app.update.enabled", false);
user_pref("extensions.torlauncher.prompt_at_startup", false);
user_pref("extensions.torbutton.no_updates", true);
user_pref("extensions.torbutton.show_slider_notification", false);
user_pref("extensions.torbutton.updateNeeded", false);
user_pref("extensions.torbutton.versioncheck_enabled", false);Restart Wireshark and launch Tor Browser again. After about 60 seconds we get:
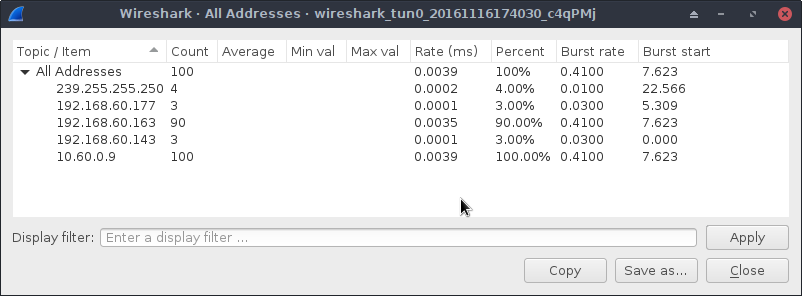
Down to 90 packets. Please note that all the configuration values above are likely not necessary, but over time we accumulated a lot of “suspects” while getting the traffic down by trial-and-error.
In Browser/TorBrowser/Data/Browser/profile.default/extensions, extract
https-everywhere-eff@eff.org.xpi into a folder named
https-everywhere-eff@eff.org and then delete the .xpi file. Open
https-everywhere-eff@eff.org/components/ssl-observatory.js and comment
out line 405:
if (topic == "browser-delayed-startup-finished") {
//this.testProxySettings();
}Restart Wireshark and launch Tor Browser again. After about 60 seconds we get:
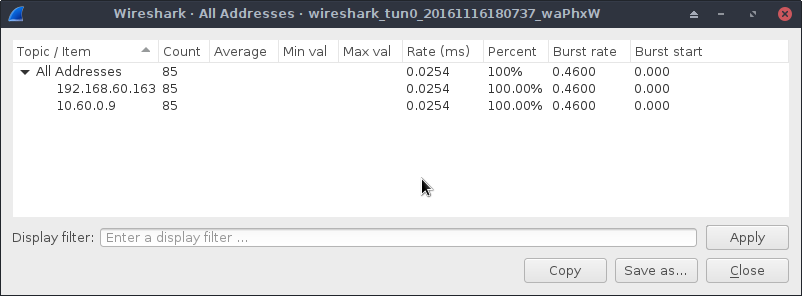
Down to 85 packets. In terms of network traffic, this is as good as we managed
to get it without interfering with how circuits are constructed in the
background. As a final trick for data collection, in Browser/TorBrowser/,
create a file named redirect.html with the following contents:
<meta http-equiv="refresh" content="10; url=https://www.kau.se/" />By using the refresh HTTP header we delay Tor Browser by ten seconds for the
site visit (to https://www.kau.se/ in the example
above). Restart Wireshark, open a terminal, navigate to Browser/ and run:
./start-tor-browser redirect.htmlLooking at Wireshark output we now see:
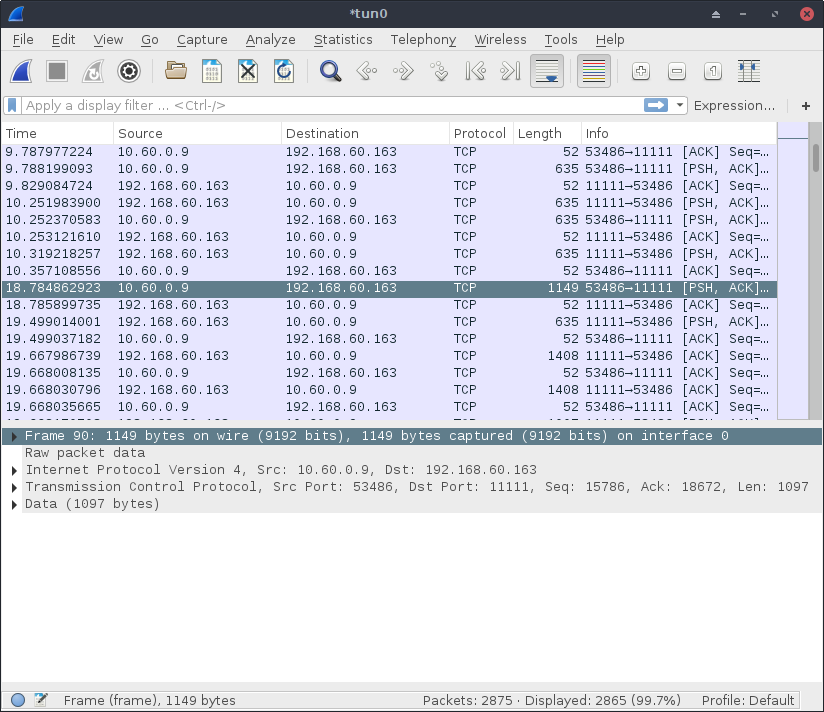
Note the over eight seconds of silence in traffic. Presumably, most of the changes we’ve made to Tor Browser together with a reasonable delay before visiting a site removes a significant amount of noise from our packet captures. Once we launch Tor Browser, we just wait around ten seconds until we start the packet capture. While not perfect, it’s probably good enough and realistic: we still cannot remove, e.g., control cells—but neither can a realistic attacker in the WF setting—and any noise on the wire generated by tor or Tor Browser is still very much encrypted and mixed in with the rest of the network traffic. By making the changes described above we’ve primarily eliminated network noise generated when starting up Tor Browser, which—relative to the number of sites visited by a user—presumably is relatively rare.